Compliance
Basic Concept Regarding Compliance
In 2004, the 50th anniversary of our company's founding, we established the "Compliance Declaration," in which top management expressed their commitment to compliance with the aim of becoming a company trusted by society both in name and reality, and to achieving sustainable development and growth. We also formulated the "Tachi-s Ethics Code," which concretely outlines behavior standards based on corporate ethics. In addition, to ensure that corporate activities based on the Tachi-s Code of Ethics are reliably upheld, we have established the "Compliance Operation Regulations," which define the operational organization related to compliance and measures to be taken in cases of violations of the Code of Ethics, and the "Internal Reporting Regulations," which specify the operation of the internal reporting system. We have put in place a system to ensure that all officers and employees comply with laws and regulations and conduct corporate activities based on corporate ethics. Our company, based on these declarations, principles, and various regulations, considers enhancing our self-purification capabilities as an enterprise and promoting sincere corporate activities, while continuing to be a company trusted by all stakeholders, as the foundation of corporate management.
Compliance Declaration
Thanks to the efforts of many over the years, the TACHI-S Group has earned a reputation as a sincere and earnest
company with technological capabilities and has built its current position through this trust. We will sincerely
strive to continue to be a company that is trusted by society, because we recognize that this is an absolute
requirement for corporate growth and development. As we celebrate the 50th anniversary of our founding, we have
clarified our code of conduct and established it here as the “TACHI-S Code of Ethical Practice.” We will
make this Code of Ethical Practice the basis of our actions and strive to practice the following.
- We will fully consider our impact on the environment, provide products that are useful and safe for society,
ensure corporate transparency, and strive to live up to the trust of all our stakeholders.
- We will comply with all laws and rules, including the spirit of such laws and rules, both in Japan and abroad,
and act with social common sense.
- We will act responsibly and cultivate ethical values as a good corporate citizen, based on the spirit of our
company motto, “Cooperation Through Mutual Compromise.”
We hereby pledge to comply with the “TACHI-S Code of Ethical Practice” and to promote compliance-based
corporate activities.
Developed April 25, 2004
Compliance Promotion System
Compliance System
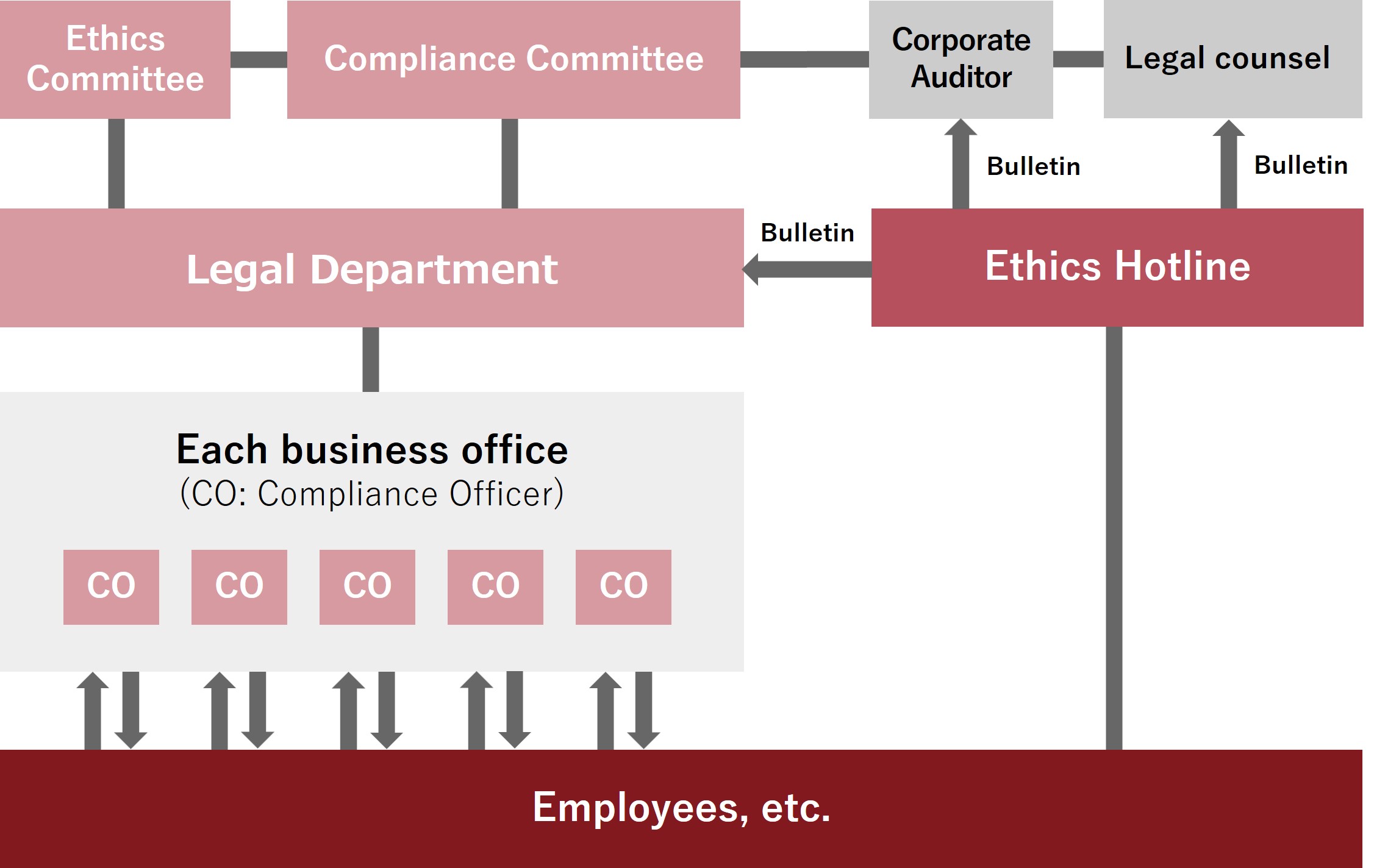
Ethics Committee
The committee is chaired by the President and consists of all Directors and relevant Executive Managing Officers as
committee members. It plays a role in maintaining and strengthening the compliance system (Secretariat: Management
Audit Office, held once a year in principle).
Compliance Committee
The committee is chaired by a Compliance Officer and consists of Outside Directors, Corporate Auditors, and legal
counsel as committee members, and is responsible for directing investigations into the facts of cases involving
violations of ethics or laws and regulations, and for making recommendations on such violations (Secretariat:
Management Audit Office, convened by the committee chair as necessary).
Compliance Officer
A corporate ethics officer assigned to each business site regarding compliance,
and is responsible for providing advice on consultation from employees and supporting the operation of the compliance
system.
Raising Awareness of Compliance
We formulate compliance action plans every year with the theme of “Each and every employee should view
compliance as a matter of familiarity and practice it in their daily work,” and we conduct the following
educational activities.
Activities to raising awareness of compliance
- Conducting compliance education for all employees at certain times after joining the company (e.g., new employee
or new manager education), and at different levels.
- A corporate ethics workshop is conducted each year as part of Corporate Ethics Reinforcement Month by an outside
lecturer for Directors, Managers, and representatives of domestic subsidiaries.
- Regularly publishing the “Compliance Letter,” which communicates familiar compliance cases in an
easy-to-understand, four-panel cartoon format, and the “Compliance Mail Magazine,” which contains news
of public interest and mini-tests.
Compliance training session
Compliance education is conducted for all employees at key milestones after joining the company (new employees, newly appointed managers, etc.) and by hierarchical levels.
Additionally, every year, as part of the Compliance Awareness Strengthening Month, directors and employees, as well as directors and employees of domestic affiliated companies, participate in compliance training sessions.
The “TACHI-S Handbook” used to raise awareness
We have compiled regulations such as “Compliance Declaration”, “Compliance Management Regulations”, “Internal Reporting System Standards” and “TACHI-S Code of Ethical Practice” into a compact, easy-to-carry handbook.
Furthermore, we have compiled a “Do's and Don'ts” as a collection of specific examples of the “TACHI-S Code of Ethical Practice” distributed to employees, and posted on the intranet to spread awareness of compliance.
Sending email newsletter
We regularly send out "Compliance Newsletter", which conveys familiar compliance cases in easy-to-understand four-panel comics, and "Compliance Mail Magazine", which includes news and mini-tests that have captured the public's interest.
Internal Monitoring
To comply with laws and regulations and engage in ethical corporate activities, we believe it is important to develop
and operate an “internal monitoring system” to serve as a foundation for preventing injustice and
unethical behavior, and for identifying problems at an early stage should they occur. An “internal reporting
system” has been established at all Group companies to handle consultations and reports on fraudulent, illegal,
or unethical activities by organizations or individuals, as well as violations of our own Code of Ethical Practice and
internal rules. �In addition, we regularly conduct “business audits” to confirm appropriateness,
compliance, and effectiveness of operations in departments that execute business. During these audits, we also check
the status of ethics and legal compliance.
Furthermore, we conduct annual compliance awareness surveys of our employees to ascertain their level of understanding
and awareness of compliance, and we use this information in educational activities.
Risk Management
Basic Approach
As the environment surrounding companies has greatly changed and the risks we face have diversified, we have established a system that enables us to respond quickly and accurately. We have positioned risk management as one of the most important management issues, and are promoting sustainable management and strengthening governance.
Risk Management System
The chairperson of the committee is the president, and all directors and executive officers except outside directors are members. We have established a Risk Management Committee that deliberates and makes decisions related to risk management for the entire group.

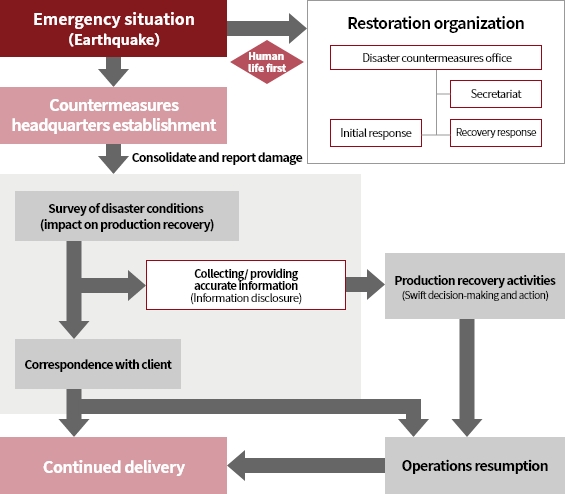
Business Continuity Plan (BCP)
We have formulated a Business Continuity Plan (BCP) to minimize damage and swiftly restore operations in the event of
a major disaster or accident occurrence. Specifically, assuming the occurrence of a major earthquake, the scope of
production restoration and the flow to restore production are defined to restore production activities as soon as
possible.
Production recovery scope
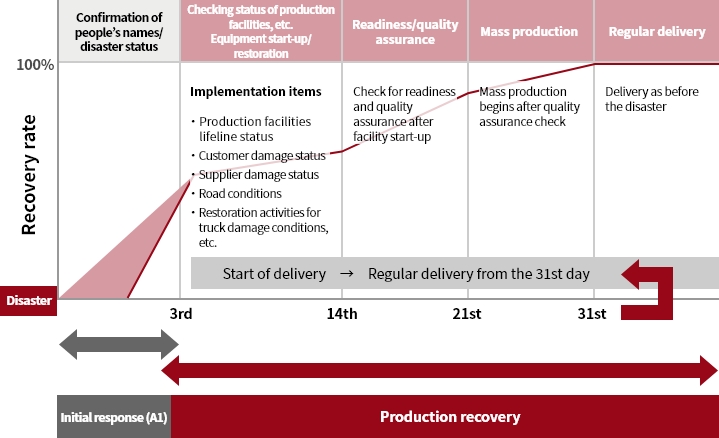
Production recovery flow in the event of an earthquake
BCP training

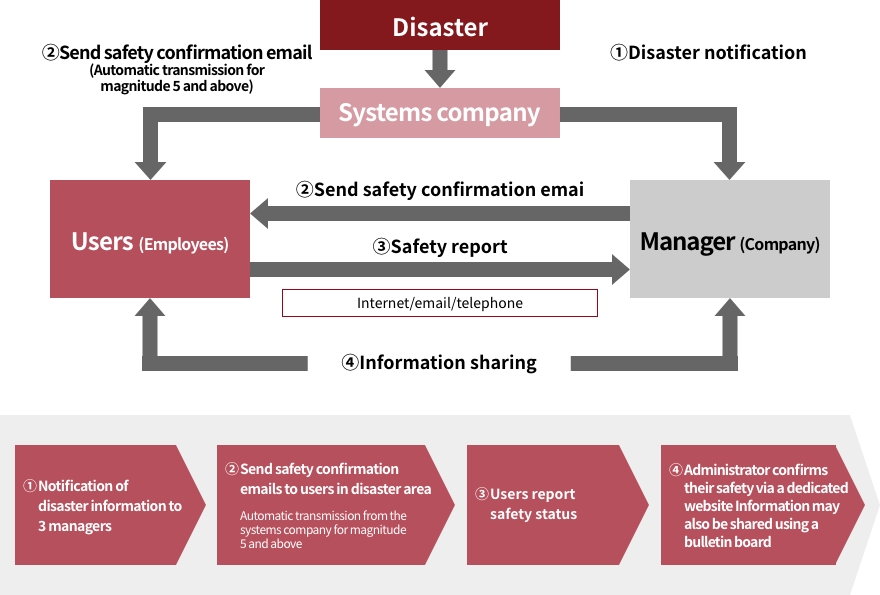
Implementing a System to Confirm Employee Safety
In the event of a disaster, it is imperative that employee safety be confirmed, means of communication secured, and
information shared. Based on the necessity to introduce an efficient and reliable system, we introduced a safety
confirmation system from a systems company as a means of confirming and communicating the safety of our employees in
the event of a disaster or other emergency as part of our disaster prevention system. In addition, regular training is
conducted to ensure that employees are proficient in system operation and that the system is operating normally.
Internal Reporting System
The Purpose of Introducing the Internal Reporting System
The purpose of the Company shall be to prevent, detect and correct misconduct at an early stage by establishing a system for appropriately handling reports or consultations on actions with compliance issues at the Company, thereby contributing to strengthening the compliance system.
Internal Reporting System Structure
The name of our internal reporting system is the "Ethics Hotline". All TACHI-S employees,and all employees of the Tachi-S Group, such as the Company's officers, employees, and other employees who have an employment relationship with the Company (temporary employees, etc.), are eligible for use and are well known.
In addition, in accordance with the “Whistleblower Protection
Act,” the contact point for reporting may be selected from among Legal Department, Corporate Auditors, or Legal Counsel, and reporting may be done anonymously. We accept reports and consultations via dedicated
telephone line, dedicated mail, E-boxes (drop boxes) set up at each office, email, telephone, in writing, and in
person.
Procedure for Consultation and Reporting to the Internal Whistleblowing Contact Point

Status of internal reports
Consultations and reports to the internal whistleblowing hotline (Tachi-s+Affiliates)

Information Security
Basic Policy on Information Security
To protect our information assets, we have established a basic policy on information security. Based on this policy,
we will work on continuous information security measures to prevent information leaks and other problems from
occurring and maintain the trust of our customers. Our Information Security Policy is a clear statement of the
policies and standards set to protect the information assets of the organization and consists of the following.
Information security policy system
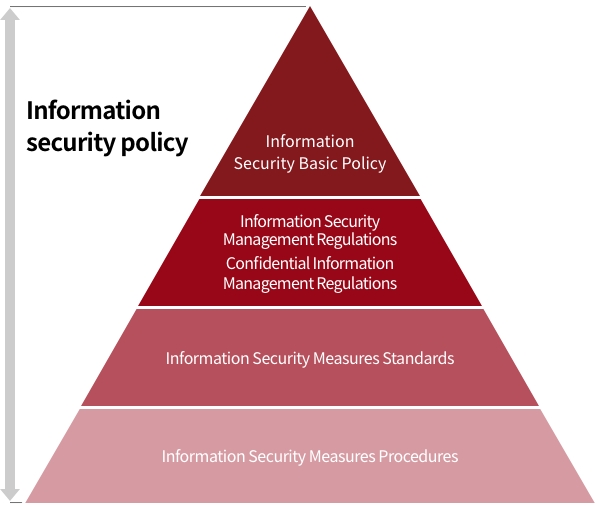
Information Security Policy
- 1. Subject of Information
Information assets are not limited to hardware, software, networks, and files. They also include documents
necessary for business, information obtained in the course of business, knowledge, and knowhow.
- 2. Proactive Measures for Information Assets
Our information assets will be used as effectively as possible and appropriate information security measures will
be implemented in accordance with the given asset’s level of importance.
- 3. Incident Response Measures
In the unlikely event of a breach, the cause of the breach will be swiftly identified and action will be taken to
minimize damage.
- 4. Promotion System
With the understanding and support of Directors, the Risk Management committee and Information Technology Department shall be responsible for development and operation of a company-wide information security system.
- 5. Education
Awareness and education activities regarding information security will be continuously conducted for all
employees, including Directors and contract employees.
- 6. Employee Obligations
All employees, including Directors and contract employees, shall understand the Basic Policy on Information
Security and act in accordance with the relevant regulations.
- 7. Penalties
Strict measures will be taken against those who violate the Basic Policy on Information Security and related
regulations.
Developed March 27, 2007
Revised June 1, 2023
Initiatives to Strengthen Information Security
To raise employee awareness of the necessity and importance of information security, in February and March, which is
the government’s “Cyber Security Month,” we conduct employee education using our internal portal to
check the level of understanding. In addition, to promptly inform employees of information security threats and
prevent information leaks, an internal portal for “security incident alerts” and an information security
contact point have been set up, and we are always working with employees to respond to problems.
The security system is divided into entry, exit, and individual countermeasures, which are periodically evaluated.
Entry countermeasures prevent viruses from entering the company through email, web browsing, or external attacks. Exit
countermeasures prevent information leakage outside the company in the event that an internal computer is infected
with a virus. Individual countermeasures include software to monitor computer behavior and controls that block the use
of USBs to prevent direct introduction of viruses. Security systems are already installed for both entry, exit, and
individual measures. In addition, these systems are monitored 24/7/365 to ensure protection from viruses.
To respond to information security risks that continuously occur, we are strengthening our countermeasures and
monitoring on a regular basis. We also take comprehensive information security countermeasures to ensure that our
employees can use our IT environment safely.
Countermeasures against information security risks in IT usage environments
Ongoing enhancements focused on countermeasures against increasingly sophisticated cyber attacks
- External/internal communication restrictions (communication restrictions and record keeping)
- Incoming email virus and spam prevention
- Public server attack prevention
- Remote connection security enhancement (authentication)
- Measures against information leaks when sending mail
- Control of dangerous internet browsing
- Virus infection from internet browsing and unauthorized communication countermeasures
- PC information leakage countermeasures (device encryption)
- Unauthorized external media connection restrictions (operation record retention)
- PC and server virus protection and monitoring